Want to fully secure your business data? Read on to know what is AWS security audit and how you can conduct it to avoid data breaches and other issues and check Best AWS Security Practices.
No doubt cloud services are faster, cheaper, and easier to use than building your own IT infrastructure from scratch.
For instance, the most popular cloud provider, AWS, offers cloud computing resources and tools for creating databases, managing identities, and access, storing data, communicating with customers, and so on.
Businesses from all over the world are using it to manage their business and customer data.
However, leveraging AWS without ensuring security can easily expose your data to hackers. This is where AWS Security Audit comes into play. In this guide, we’ll look into:
- What is AWS Security Audit?
- How to Conduct an AWS Security Audit?
What Is AWS Security Audit?
In the context of IT, an ordinary security audit involves reviewing how to secure network infrastructure by evaluating its various aspects, including permissions, configurations, app logic, etc.
The aim is to ensure that the infrastructure is vulnerability-free and follows established security standards.
On the same lines, AWS Security Audit has to do with inspecting an AWS instance for security gaps, vulnerabilities, loopholes, and misconfiguration. It has two basic categories:
Security in the Cloud:
This part of the AWS security audit is your responsibility. By selecting what you decide to implement and how you want to do it, you can fully control the security of your AWS instance.
You can prevent hackers from gaining unauthorized access to your web app by configuring it securely.
Security of Cloud:
The security of the cloud is taken care of by AWS itself. It includes preventing or addressing all the zero-days or logic flaws that may be utilized to exploit the server’s instance.
Now that you have a basic idea of AWS Security Audit, let’s find out how to audit an AWS account:
How to Conduct Audit an AWS Audit: Guidelines + Checklist
The last thing you want to be happening to your company is a data breach that can ruin the trust of the customer forever.
- If a single AWS instance is vulnerable, your entire customer and business data is put at the mercy of hackers.
- And if a data breach does occur, it can adversely impact the reputation of your brand, the trust of the customer, and your profitability.
- Hence, you should conduct an AWS Security Audit, which may include a review of system logs every month, and a full scan to ensure that a breach did not happen during any year.
- And an inspection of the hosted service’s behavior for something suspicious or abnormalities every six months.
Follow these steps to audit your AWS account:
Step 1: Generate and Manage a Complete Assets List
An asset in the AWS space refers to anything with an identifier, including servers, policies, and roles.
When you possess a list of these resources, you can begin to determine what they do, whether or not any of them have been misconfigured, and how to protect them.
You can build an asset inventory in various ways. You may use CLI scripts or third-party tools, but AWS config represents an easier and quicker way that enables you to record and inspect the configurations of your AWS resources.
Step 2: Develop a Strategy for IAM
Have a solid strategy in place for identity and Access Management. If not anything else, be sure to do the following:
- Configure the password requirements.
- All user accounts, particularly the root account, should have MFA implemented.
- With the exception of changing its address and setting the billing plan, the root account offers no extra function that can’t be performed as an actual IAM user, so don’t use that account.
- Keep an eye on unintended access using Access Analyzer, which will show you roles that outside entities can assume.
- The greater the use of IAM users, the higher will be the risk, so try to limit their use as much as you can.
- For human access, utilize AWS SSO and create job-specific roles that humans can assume. This way, life will be much easier for developers.
- Give access to users based on job role, not the individual.
- If a role hasn’t been used for 90 days or more, disable it. In the next 90 days, if no one complains about it, delete the role.
- For IAM analysis, use third-party/open-source tools.
Step 3: Locate Public Resources
Once you’ve developed an assets list and a strategy for IAM, it’s time to take on public resources, which are anything labeled as public and thus pose risks such as databases, AWS S3, SNS, EBS snapshots, and so on.
- Other than S3 misconfigurations, there are various other public things that are dangerous, yet go overlooked.
- For instance, some people would take servers’ snapshots and mistakenly configure them to be public.
- The reason why it’s critical to identify publicly available resources is that they can cause unintended access to services and accounts, data loss, and data exfiltration.
- Examples of resources that are unintentionally public include EC2 instances, S3 objects or buckets, databases, snapshots, and SNS topics.
- If you think about it, there’s no reason for an S3 bucket to be public. Therefore, enable the S3 Public Access block at the account level.
Apply IP security rules to all VPCs by using AWS Firewall Manager and turn GuardDuty on. You may also use managed config rules, but this doesn’t mean you shouldn’t write your own.
Step 4: Leverage AWS Organizations
AWS Organizations are among the most powerful mechanisms in your AWS security toolbox, yet they’re one of the most underrated things you can do for AWS security.
An account serves as a border, with you deciding what things are allowed in and out of the account. Unless you allow, nothing can enter or go out by default.
Based on the recommended AWS Organization structure, there’s a Management/Root account that hosts the organization.
Each of the Production OU, Development OU, Pre-Production OU, and Build OU possesses one service or account. The Operations OU has Corp systems accounts and DNS accounts.
The security account that’s the owner of all security tools and the logging account, which represents the source of truth for all logs security uses, both come under the Security OU.
Any unused or closed accounts are kept in suspended OU, which has SCP to prevent any actions.
Step 5: Make Sure Audit Logs Are Enabled
Then you need to have audit logs, which are crucial for detecting notable events and letting you uncover what has happened after an event.
One solution that serves as the auto-log of each action that happens in AWS is CloudTrail. Plus, you may consider other services like S3 access logs when using buckets publicly or VPC Flow Logs if you’re using servers.
Some of the basic steps include ensuring that CloudTrail is enabled and logs are stored in S3.
At the same time, the S3 bucket should be subject to highly restricted access. Ideally, all logs should be stored in a single dedicated account. In addition, turn on Global CloudTrail when using AWS Organizations.
If you’re looking forward to using CloudTrail, bear in mind that it can quickly become expensive, particularly if you’re storing in S3.
Step 6: Switch on Security Controls
Turn on Inspector, Guard Duty, and other native security tools. Guard Duty is a great option.
However, if you’re running EC2 instances without a strong vulnerability management program, you should be better off with an Inspector.
By turning on Inspector, you should be able to find the missing patches and things of that nature.
Step 7: Create Network Maps and Data Flow Diagrams
If you’re not aware of how the developer is leveraging the system, you won’t know what to do, which is why you should have data flow diagrams of everything.
When it comes to making decisions like blocking S3 public access, this can be of great help.
Step 8: Choose a Standard
Don’t stick to an approach of implementing a rule when you’re faced with an issue. You need guideposts as part of your efforts to conduct an AWS security audit.
This is what standards are designed for. Popular standards include CCM, NIST CSF/800-53, and CIS. Use them to make informed decisions, but don’t consider them as rules.
Step 9: Track Findings Through a Risk Register
Like assets, risks need to be tracked. To ensure that you’re fire-preventing instead of fire-fighting, consider building a risk register, which can simply be a spreadsheet that tracks the following things at a bare minimum:
- ID– the finding’s dedicated identifier
- Status– the risk’s current status
- Priority– Criticality indicator
- Description– explanation of the risk
- Likelihood– the chances of a scenario happening
- Impact– Result of the occurrence
- Response Type- Transfer, Avoid, Mitigate, Accept
- Response Description- how can the risk be mitigated or resolved?
- Owner– The responsibility falls on whom?
AWS security audit tool
AWS provides multiple options for Security Audits. Let us check out a few among them.
AWS Audit Manager – It audits your system continuously and gathers audit information. It also provides read access to the users to act on the information.
AWS Macie – Macie is a wonderful tool that continuously scans the data in the S3 buckets for any PI data and keeps the owners informed about it.
AWS Inspector – Assessment and Monitoring for the apps deployed in EC2. It checks the security vulnerability of your EC2.
AWS Cloudwatch, CloudTrail, and VPC FlowLogs – These are the backbone of your monitoring in AWS. These three collect your logs and that can be used to monitor the security of your system.
Amazon Shield – Protects the infrastructure against DDoS attacks.
Amazon GuardDuty – It keeps monitoring your AWS accounts to check for any wrong or malicious activity and keeps the users posted about the same.
What is the AWS audit manager?
AWS Audit Manager is the tool to go when you want your systems to be continuously audited and the logs to be stored for the user’s reference. This app also gives read-only permission by default to view the logs.
AWS security audit role permissions
Below is the terraform code that describes the role that you can create to give the security audit roles the permission to work in the AWS environment.
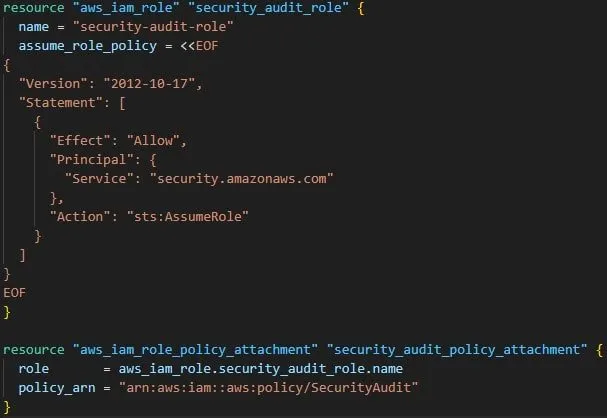
AWS security audit managed policy
Below is the terraform code that creates the Security Audit Managed policy in the AWS, let us check that out.
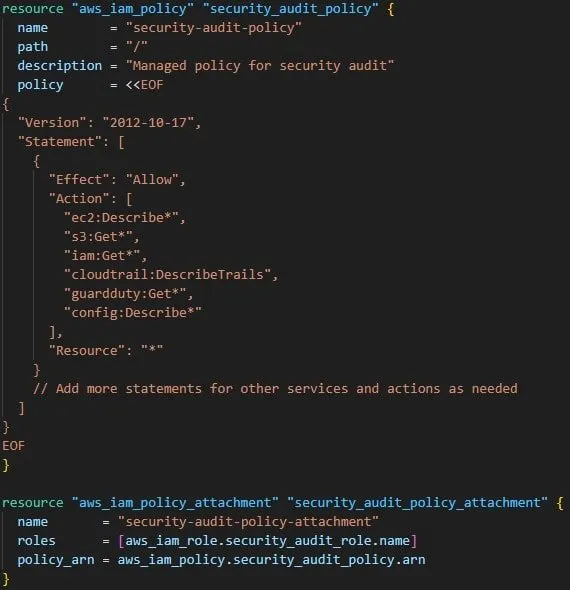
AWS security audit Is readonly
Audit logs are by default given read-only permissions to the users for viewing the logs and taking necessary action as required.
AWS security audit reports
Once the assessment of your systems is done the system generated the report with the collected audit information.
The details of the report depend on the parameters you pass during report generation.
This report helps the user to collect and audit the evidence of his system. This detailed evidence can be shared with the auditors for further analysis.
Conclusion
Now that you have obtained an in-depth understanding of AWS Security Audit, it’s time to secure your AWS account.
Follow the aforementioned tips to conduct an effective AWS Security Audit. We truly hope that this guide helps you fully secure your business and customer data on AWS.
Keep Clouding!!

I am an Amazon Web Services Professional, having more than 11 years of experience in AWS and other technologies. Extensively working in various AWS tools like S3, Lambda, API, Kinesis, Load Balancers, EKS, ECS, and many more. Working as a Solution Architect and Technology Lead for Architecting and implementing the same for different clients. He provides expert solutions around the world and especially in countries like the United States, Canada, United Kingdom, Australia, New Zealand, etc. Check out the complete profile on About us.

