In this AWS post, we will have a detailed discussion on What Is IAM AWS, How AWS IAM Works, and its various components. We will be covering the below points in detail:
- What is IAM?
- What is MFA in IAM?
- What is a User in IAM ?
- What is a Group in IAM?
- What is a Policy in IAM?
- What is a Role in AWS IAM?
- What are Identity Providers in IAM?
What is IAM In AWS?
IAM is a Global Service, it is independent of any Region. AWS IAM is the first line of defense in AWS. User management and access control is the primary objective of IAM. Being the first line of defense any user or program trying to connect to AWS has to pass through the IAM authentication process. With IAM we can create users, groups, roles, and policies in AWS.
IAM also provides the access required to use IAM AWS CLI and AWS SDK, also to make the API call, using the Access Key ID and the Secret Access Key.
- It’s a centralized place to manage all the access-related activities in AWS. It also helps to set up granular permissions to the AWS account i.e., which user or roles have what access and what access is specifically denied can also be set up using IAM.
- IAM also has the option to set up Identity Federation. You can use Active Directory, Facebook, or LinkedIn with IAM to set up user access.
- You can set up Multifactor Authentication for the user, by that not only username and password but the user who has to enter a special code to log in from tools like Google Authenticator.
- It also provides temporary access to users or devices.
What is MFA in IAM?
MFA is Multi-factor Authentication, this is additional security that should be set up with any of the user accounts in AWS.
Yes, we can access AWS with just the username and password but setting up an MFA gives an additional layer of security in any of the user accounts. Here we use tools available in Apple Store or Google store to link with AWS and set up MFA.
So the point here is How to set up MFA in AWS?
- When you log in to any of the AWS accounts you can see the below security recommendation to set up MFA.
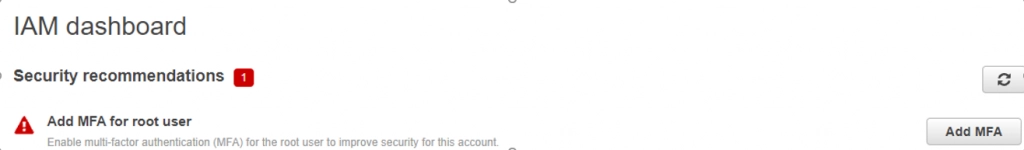
- Just follow along and click on the Add MFA button as you can see above. Then you would be redirected to the screen where you can see the below options.
- Click on the Active MFA button on the below screen.
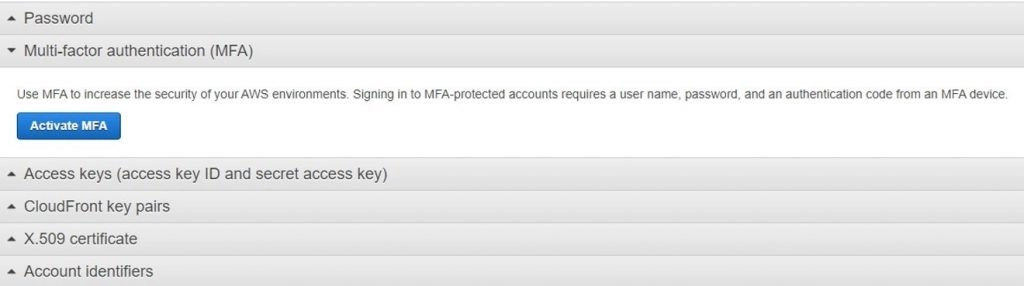
- You can see a pop-up window below with which we can see three options to set up MFA. Here we will go with the Virtual MFA Device to set it up.
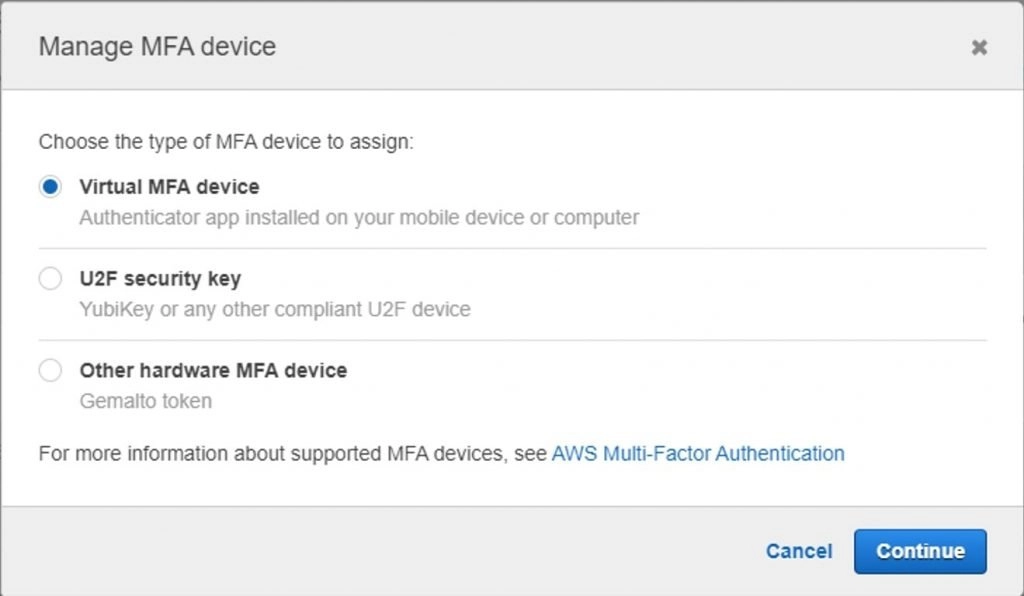
- You can use any of the authentication tools available and supported by AWS. Download the tool from the play store and open it.
- Scan the QR code displayed on the screen with your phone.
- You have to enter 2 consecutive codes which you can see on the phone in the popup window in AWS. You can see the below message and you have successfully set up MFA making your AWS account very secure.
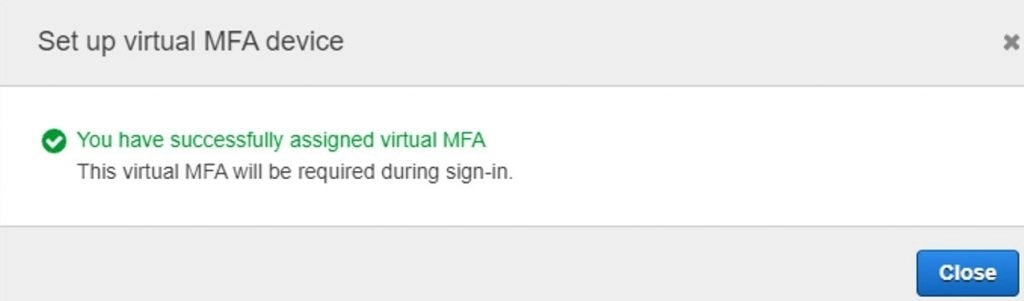
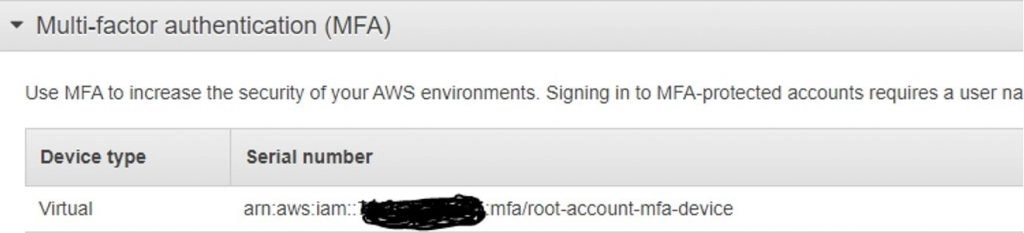
- To re-verify that everything worked correctly you can go to the initial window and you can see the details of the virtual MFA setup and linked to the account.
what is IAM user in AWS?
User has access to AWS depending on the level of permissions given to any particular user.
The user used to create the AWS account initially is the Root User and it has Administrator Privileges in AWS.
It is always recommended to set up an MFA for the Root User, in fact, the setting of an MFA is always recommended for any of the user accounts in AWS.
Never use the Root User for any of the activities in AWS, It’s always recommended to create additional users and give them permission based on the activities they will be performing in the AWS. For example, a developer does not need access to IAM, so access should be given to any user but the Sysops Admin users.
So now the question is how to create users in AWS, let’s follow along to create a user in AWS:
- In the AWS Console, navigate to the IAM screen, there you can see users, click on that and you could see the below screen.
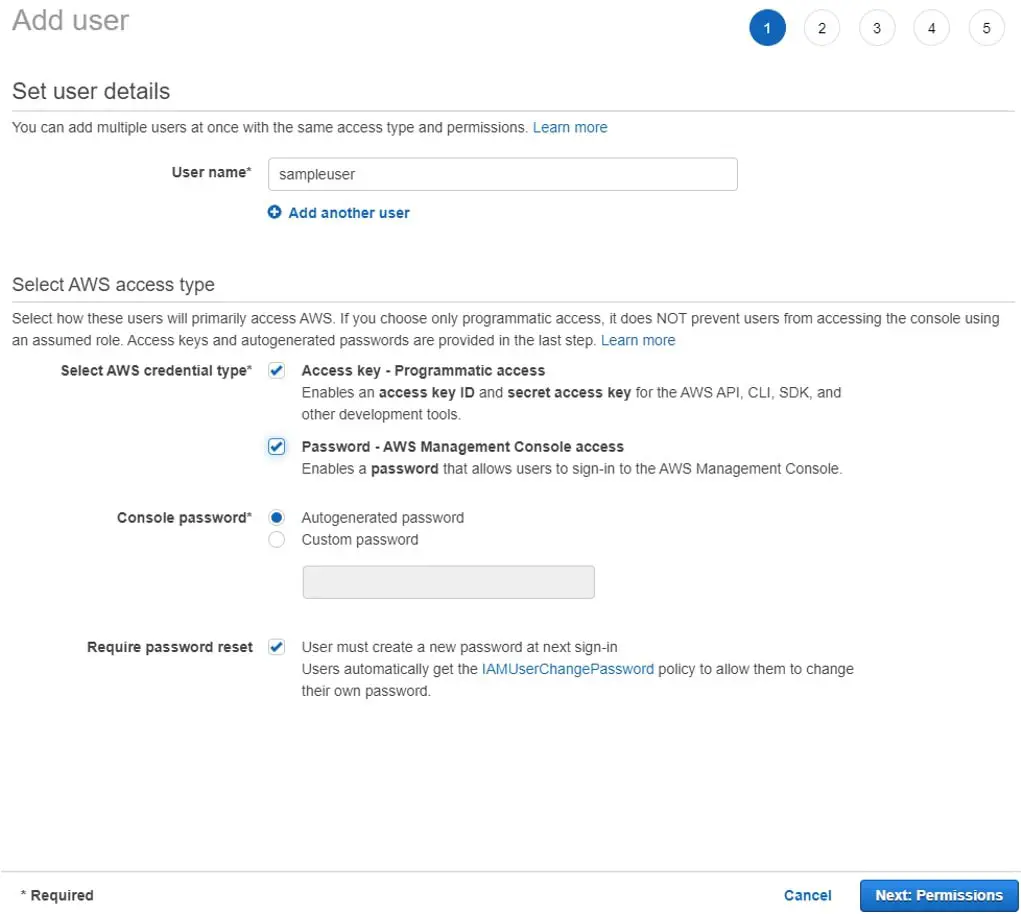
- Fill in the details such as the username of your choice, and try to make it meaningful.
- In the Credential type, you will find 2 options, you could select either of those or both.
- Access Key Credential type will provide you with an access key Id and a secret access key which can be used to access AWS through API, AWS CLI, SDK, and other development tools basically used by the developers.
- Password Credential type will give you access to the console with a username created and a password. Of course, it’s secure to set up MFA for this user the moment the user logs in the future.
- In Console Password, check the option if you would like to auto-generate the password or create a password for the user.
- Check the password reset option if you would like the user to change the password in the first login.
- You can even choose how you want the users to set the new password in AWS by setting up the below options as per the organization’s policy.
- User creation and groups always go hand in hand. It’s always recommended to create users and add them to a group and apply permissions to the group rather than to every user individually.
what is AWS IAM Group?
The group is nothing but a logical grouping of the users created in AWS. You can assign a group to a user while creating a user or that can be done later as well.
So, what are the benefits of assigning users to groups-
- In groups, users can be added and removed as per their categories.
- Permissions can be added or removed centrally, rather than doing it for every individual user.
How to Create a group while creating Users?
Follow the steps below:
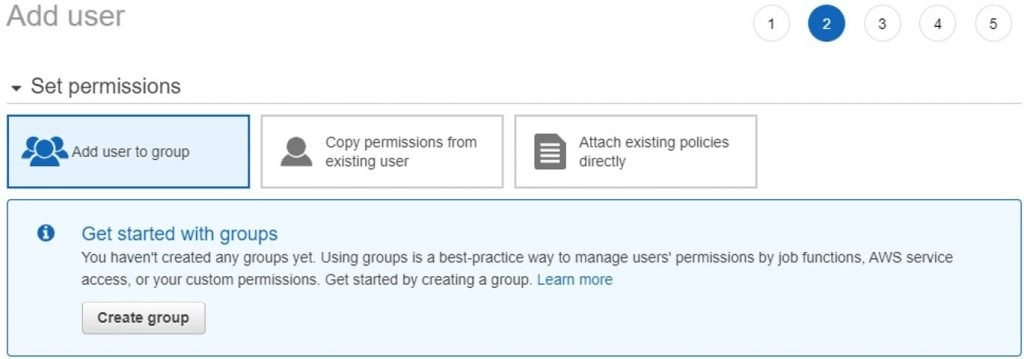
- In the 2nd step of creating users, you can see the option as shown below to create a group while setting permissions for the user.
- Click on Create Group.
- In the below screen give a name to the group that you like the users to be in.
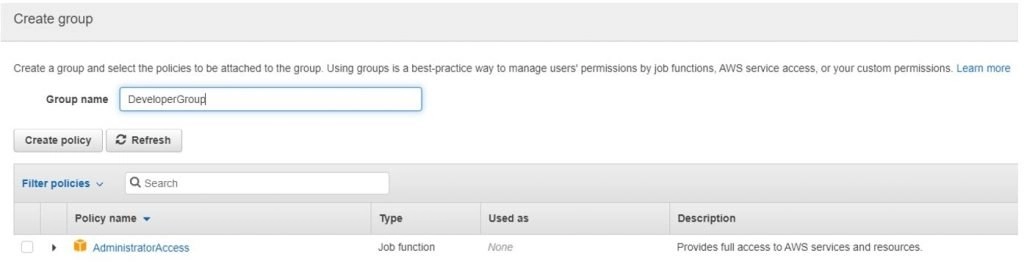
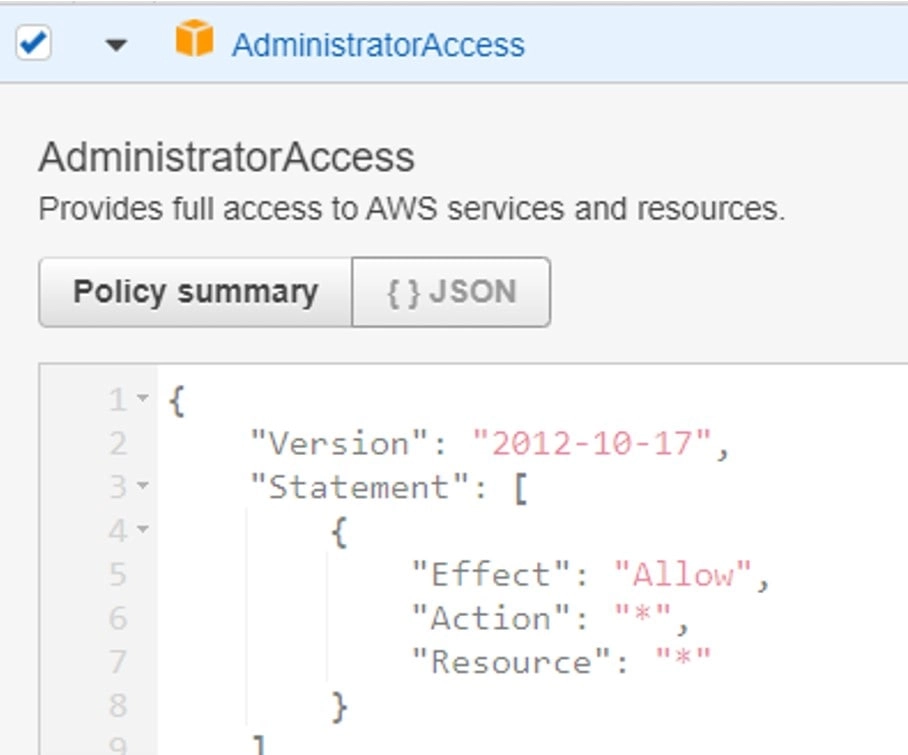
- In the policy choose only the policy that suits best the group job profile, below we can see the policy for the group.
- A policy is a JSON file that sets the permission level for the group.
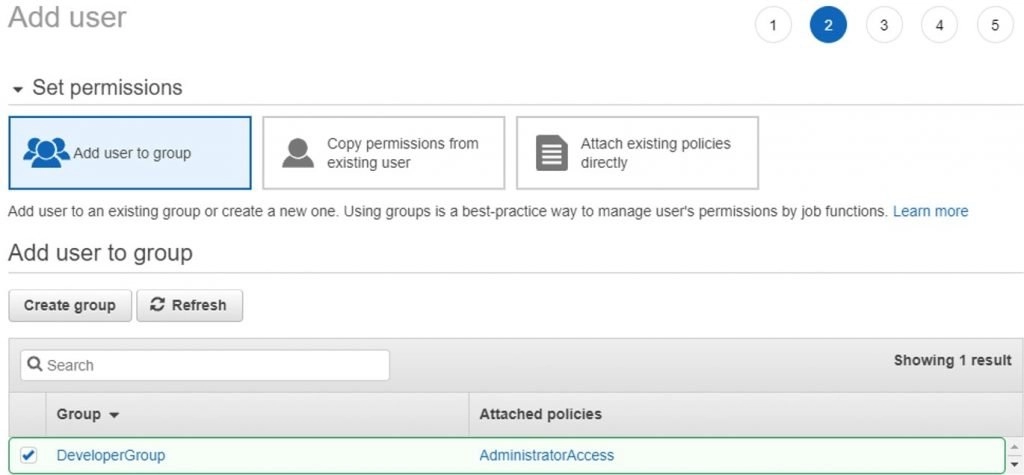
- Once done we can see the below group created with the permissions set for the group, and the user is added to the group by default as we are creating the group while creating the user.
- But if we are creating the group separately then we have to explicitly add the required users to the group.
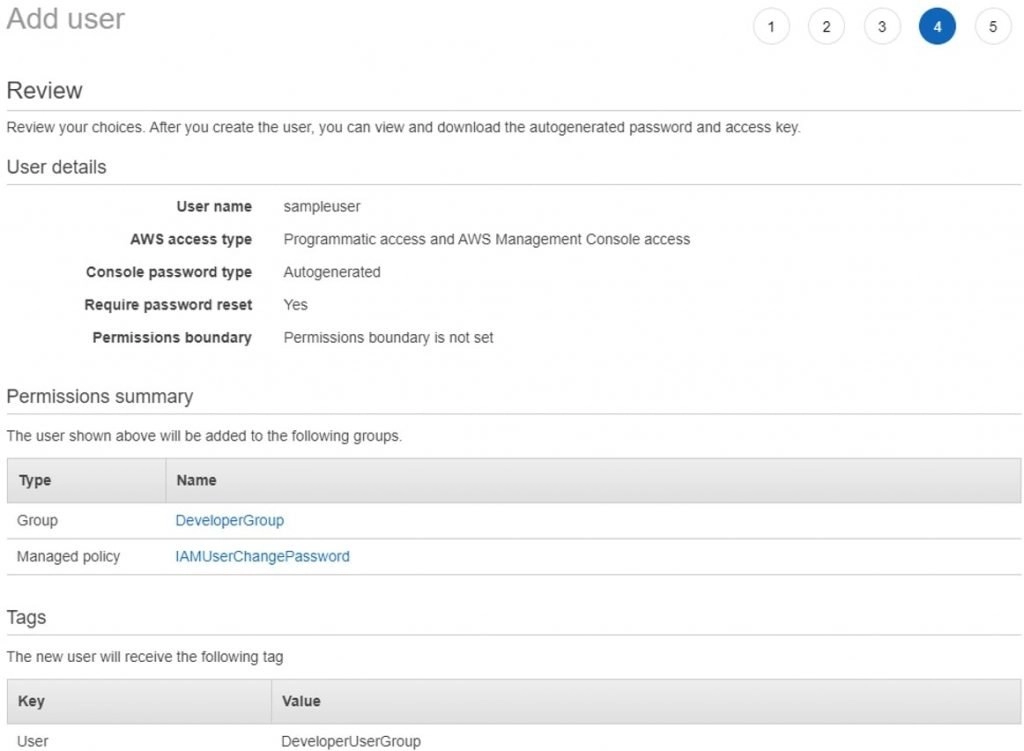
- Then we can see a confirmation screen that tells the details about the user as you can see in the below screenshot.
- That’s it we have successfully created a user and a group and the user is added to the group as well as shown below in the screenshot.
- If you remember we choose both the login option for the user i.e., Console access and programmatic access as well in the first screen.
- In the below screenshot, the user and password are for console access, and the Access Key ID, and the Secret Access key are for access through CLI, SDK, API, etc.
- It’s always recommended to download the CSV file as you can see below and save it in a safe place because once you click show in the secret Access Key or the Password you won’t have the option to view it again. So, better download and save it.
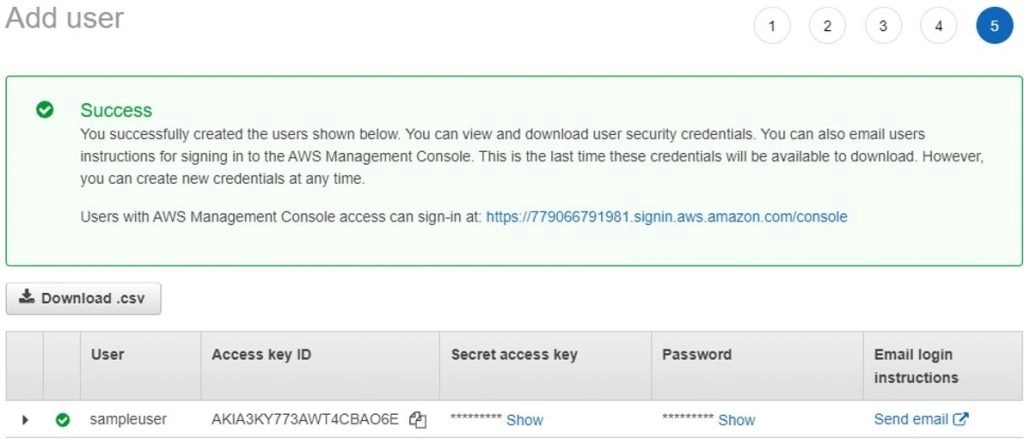
- See the User is created and the user is already added to the group.
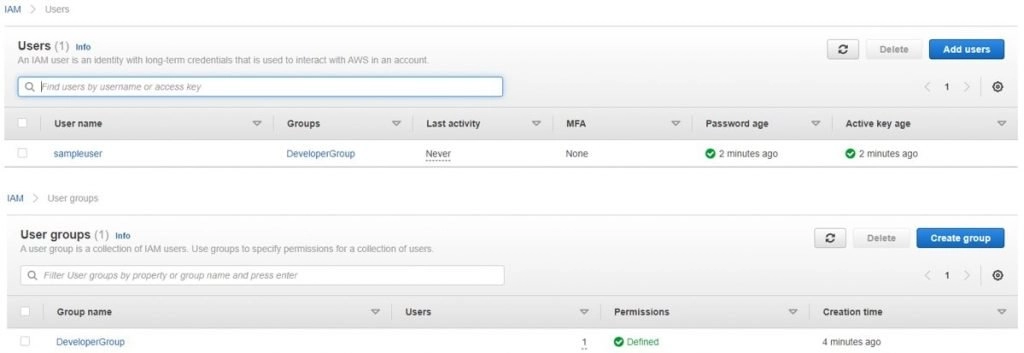
Hope you have created a user for yourself 😊!!
what is AWS IAM policy
The policy is a set of permission that is made up of documents that are stored as JSON files.
They define the boundary of what action a User/Group/Role can perform in the AWS environment.
The policy can be added to an individual User directly (Inline Policy) or Group and to a Role as well.
AWS has created many policies which are called Managed Policies, along with that we can also define and create our own policies as per the business requirement and store them in AWS, we have to write them in JSON format only. These can also be used with our User/Group/Roles.
AWS has provided an interface to create our own policies. Let’s take a look at how to do it in the Console:
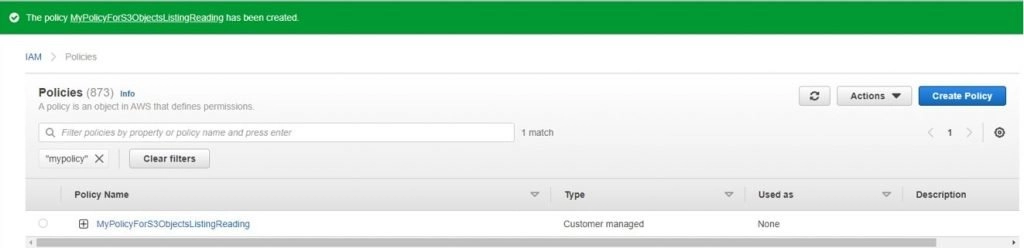
- In the IAM, click on the Policy, then click on Create Policy as you can see in the screenshot.
- Here we have the option to create a policy using the Visual Editor, where AWS gives us a step-by-step process to do. Else we can also go to the JSON tab and we can write down our own policy.
- Choose the service for which you want the policy to be created.
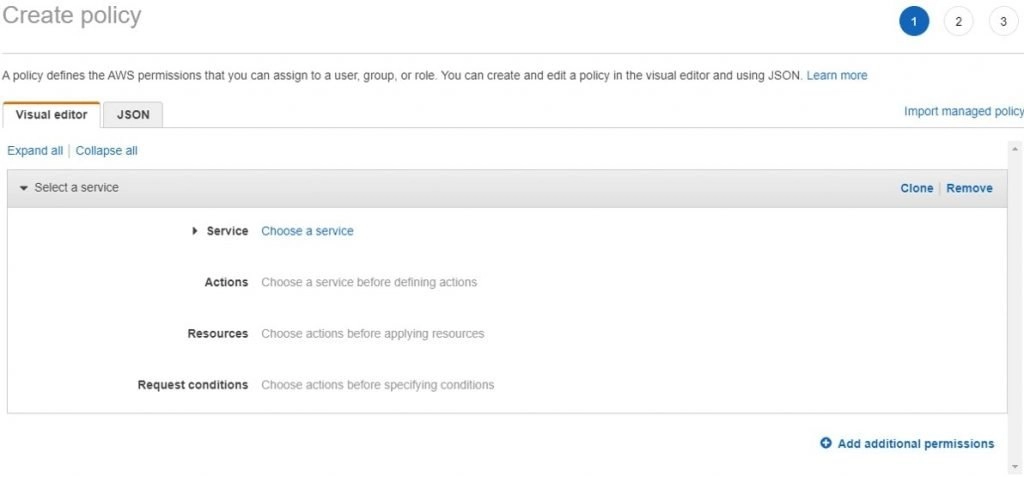
- Then specify the action which you be allowed on the service to be performed. For example, we have selected the Service as S3 and the action allowed to be performed on S3 are List and Read-only.
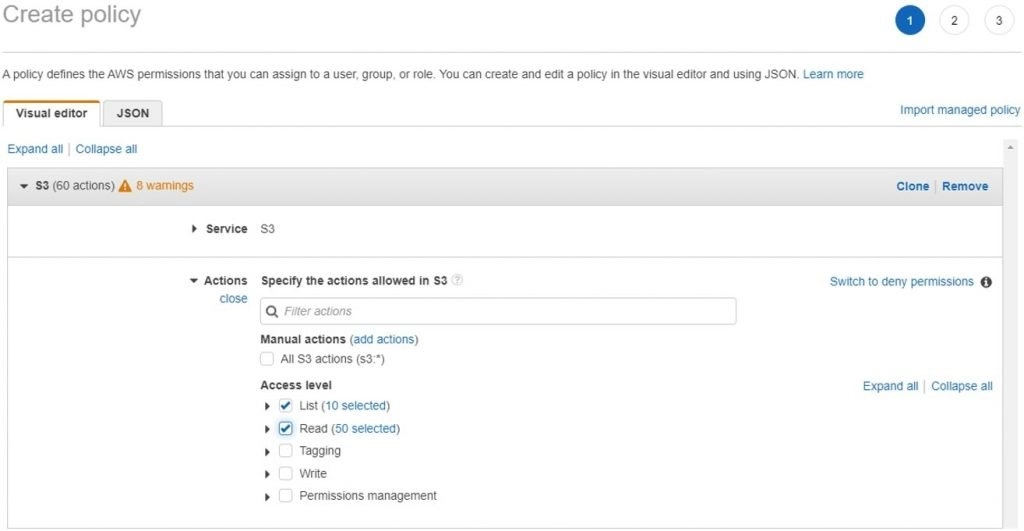
- Give a name to the policy, you can also view the details of the access level that you have chosen. Then click on Create Policy. That’s it!!
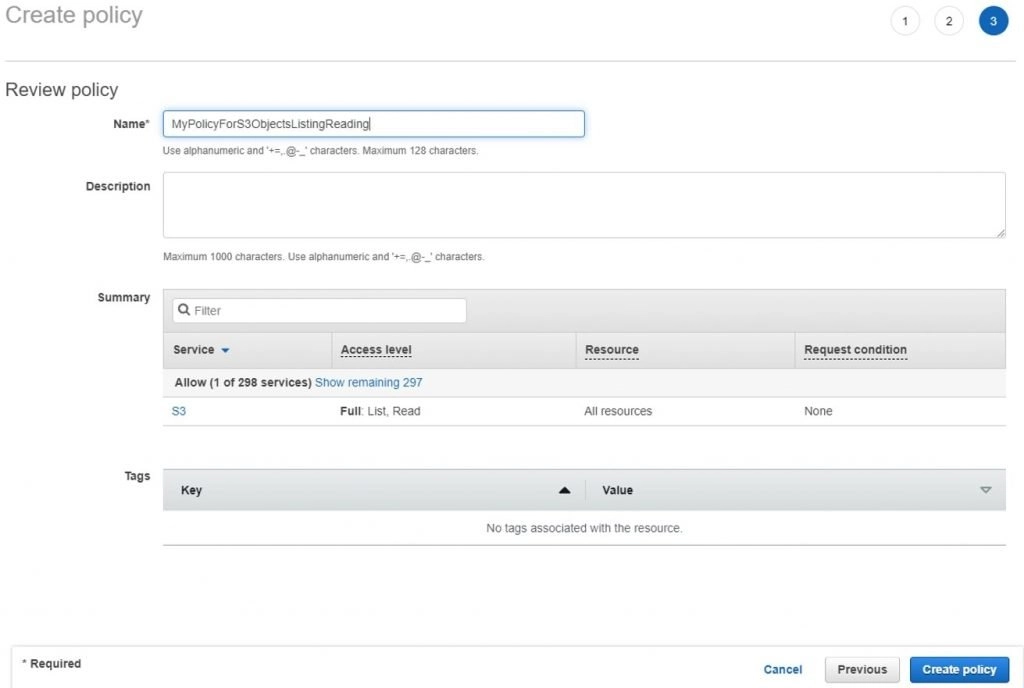
- You can see the policy in the policies list and this will be Customer Managed policy.

what are AWS IAM roles
The role is the permission that we attach to one service to communicate with another service.
We create the Role and assign them to the resources in AWS.
Basically, policies are attached to the roles which define the boundary of permission for the communicating services.
So, let’s create a Role now, shall we?
- Log in to the console and navigate to IAM, in that click on Roles.
- Click on Create Role as you can see below.
- Select a service for which you would like the role to be attached in the below screen.
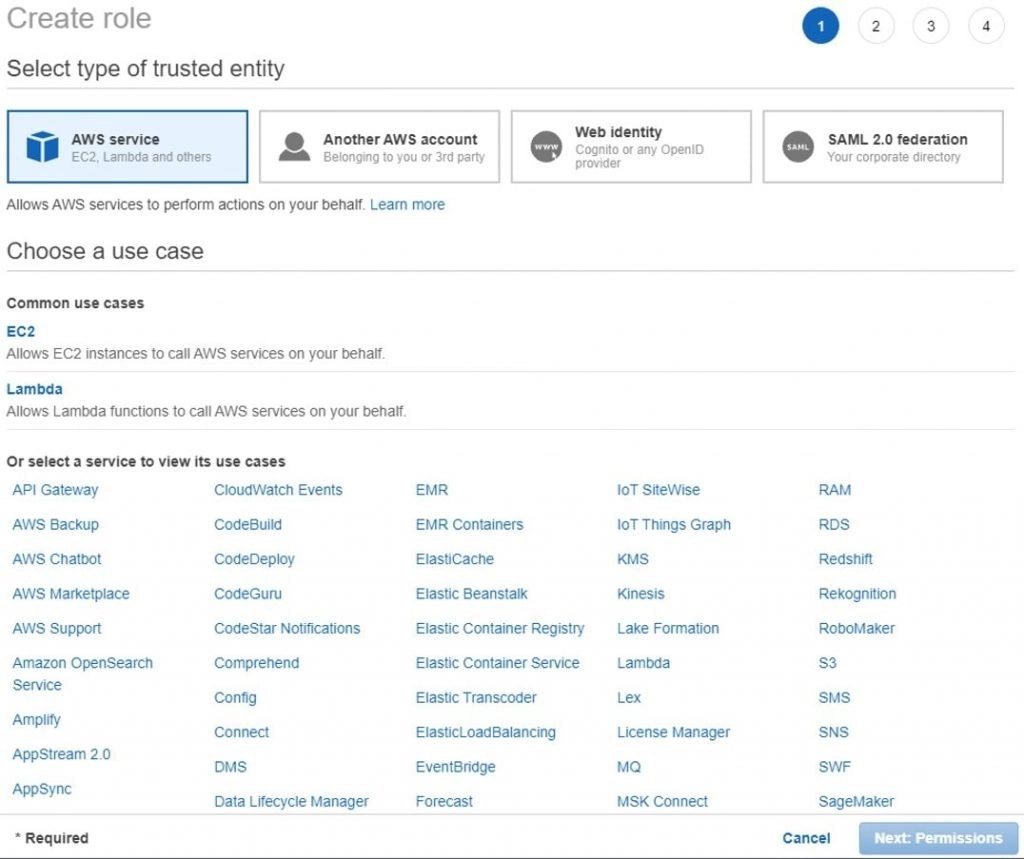
- In the next screen, you have to attach the policy which you like to use for the service you selected.
- Give a name to the role, here you could verify the service for which you are creating the role and the policy you are attaching to the role.
- Once verified click on Create role, and Voila the Role is ready to be used.
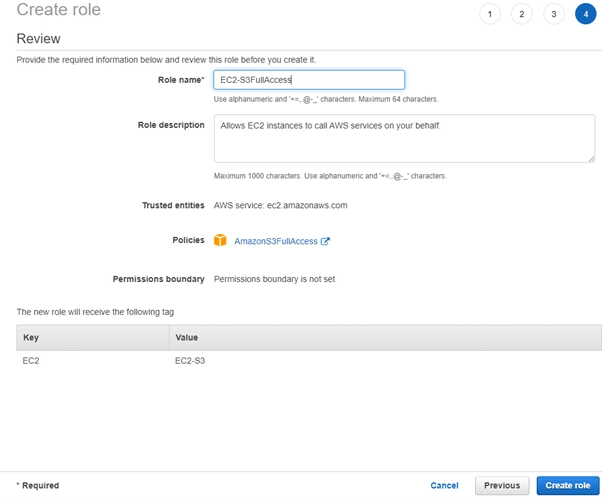
- You can verify the role you created in the below screen. It will appear in the list of roles created.

What is an Identity Provider In AWS?
It’s a tool provided by AWS in IAM which can be used to access AWS through applications such as Facebook or Twitter or a Corporate Active Directory or an LDAP.
Here the users are not maintained in AWS but they can access AWS through the Identity Provider service AWS.
We can also set up Single Sign-On for the users using Identity Providers.
IAM Best Practices to follow
Now that we have gone through IAM in detail, let’s look at some of the best practices which should be followed in IAM to keep AWS secure. As discussed earlier it’s the first line of defense for our AWS Account.
- Always set up MFA for all the users, it gives double security.
- Avoid giving direct access to the Users, attach the users to a group, and give permission to the group. It helps in better user management as well as it helps in permission management.
- Always follow the least access policy. By that we mean we should give the least access to any service or user which is required only to perform the task nothing more than that should be given.
- Keep the credentials in a safe place.
FAQs On IAM AWS
Q1: What does IAM Allow you to do?
IAM allows us to create Users/Policies/Roles and Groups.
Q2: An IAM user account is a separate AWS Account?
No, IAM is an integral part of AWS, everything created/configured in IAM is under the same AWS Account.
Q3: How IAM helps to configure AWS CLI?
IAM also provides the access required to use AWS CLI and AWS SDK, also to make the API call, using the Access Key ID and the Secret Access Key.
Q4: How to make API calls To AWS?
You can make the API calls to AWS using the Access Key ID and the Secret Access Key which you will be getting when creating the user and the user has to have programmatic access to AWS.
Q5: Which IAM policy provides full access to resources in it but not IAM?
The correct policy provider is “Power User Policy“.
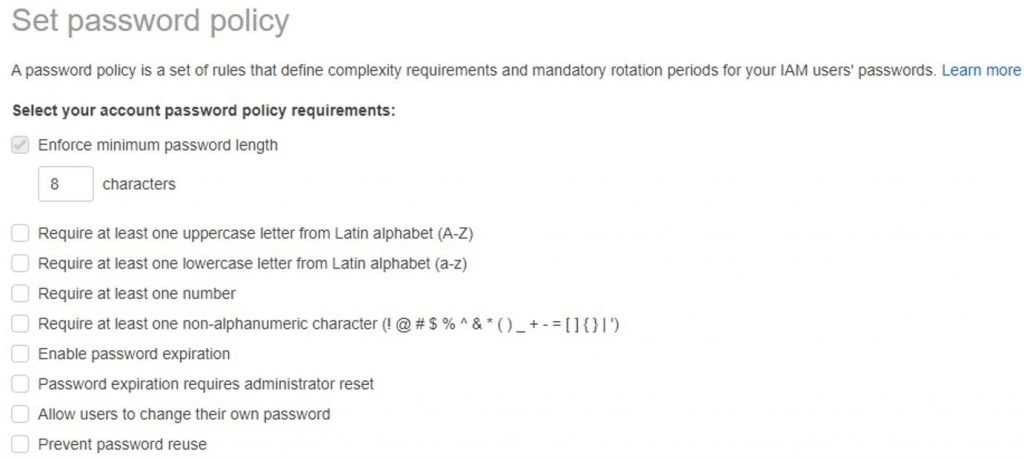
Q6: Can you set up a password policy for users in IAM?
Yes, we can do it, use the Set Password Policy in IAM to set it.
Also, find below the AWS article for more info.
- What Is AWS Lambda
- How Secure Is AWS And How Does It Work
- Hosting Websites On AWS For Free- Step By Step Guide
- Overview Of AWS Cloud Management Tools And Usages
- How To Delete AWS Account [Suspended | Partner | Training]
- Introduction To VMWare AWS Hybrid Cloud?
Conclusion
In this blog, we coved everything about What is IAM AWS and its other components like below.
- What is IAM?
- What is MFA in IAM?
- What is a User in IAM?
- What is a Group in IAM?
- What is a Policy in IAM?
- What is a Role in AWS IAM?
- What are Identity Providers in IAM?

I am an Amazon Web Services Professional, having more than 11 years of experience in AWS and other technologies. Extensively working in various AWS tools like S3, Lambda, API, Kinesis, Load Balancers, EKS, ECS, and many more. Working as a Solution Architect and Technology Lead for Architecting and implementing the same for different clients. He provides expert solutions around the world and especially in countries like the United States, Canada, United Kingdom, Australia, New Zealand, etc. Check out the complete profile on About us.

